Security in Microservices
The microservices architecture is experiencing rapid proliferation. Projections by Verified Market Research indicate that the microservices market is poised to reach $7 billion by 2030, exhibiting a substantial 22% Compound Annual Growth Rate (CAGR) from 2023 to 2030.
When it comes to microservices applications, appropriately dealing with security measures is highly important. As microservices-based software is a composition of decentralized and loosely coupled services, you risk facing tangible security threats. Especially when your app is deployed on a cloud platform. That’s why today we’re discussing various facets of microservices security, including authentication, authorization, API security, access tokens, and best security practices for creating a secure microservices ecosystem.
What Are Microservices?
Microservices constitute discreet, self-contained units within an application, each fulfilling distinct functions. These units communicate via secure Application Programming Interfaces (APIs). Microservices autonomy affords development teams the flexibility to focus on individual services without disturbing the broader application. Furthermore, each microservice can employ disparate data storage solutions and programming languages.
In contrast to monolithic applications, wherein a single process failure can cripple the entire system, microservices offer robust and secure fault tolerance. If a fault arises in one microservice, the remaining application microservice components can continue functioning seamlessly.
Security in Microservices: 3 Main Things to Remember
Following our course on Microservices basics, you already know the specifics of microservice architecture, particularly the need to use API gateways as a single-entry point for client requests. Its purpose is to provide a secure communication passage between numerous app services and a client-side by authenticating requests and forwarding them to appropriate microservices that can, in turn, invoke other required services.
The problem to solve from the security concept’s side is how to verify the identity of a client and pass it to the service that would handle a particular request.
Security Thing 1. Authentication and Authorization
These are the two terms we use for the components of the system that enforce the security control over access rights to services and apply the security policies.
The authentication technology determines whether a client is who or what it states itself to be. If the client’s credentials successfully match the credentials in an app’s database of authorized users or a data authentication server, the security identification process is passed. Then, the authentication component provides a client or a service with secure access control for other services or permission to make calls to them. The most common example of authentication technology is the login and password form.
So, to communicate with each other and external clients securely, each of your app’s services has to have a unique identity to be authenticated and authorized as a single entity. It’s not an easy security task to accomplish – your system might have hundreds of microservices of various sizes and levels of digitalization.
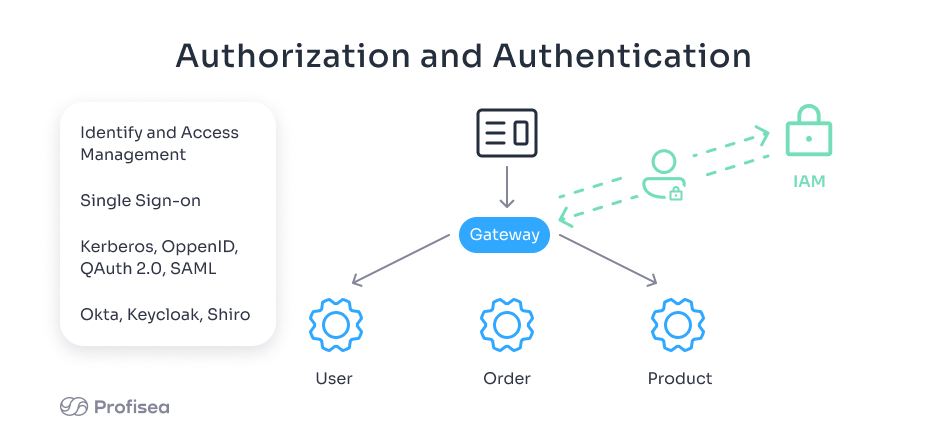 Authorization is the process of determining who to grant the privileges of use and permission to do something inside the system. It’s who is allowed to do what. Single sign-on security technology ensures that once logged in, the user won’t have to log in again and again to access the needed service.
Authorization is the process of determining who to grant the privileges of use and permission to do something inside the system. It’s who is allowed to do what. Single sign-on security technology ensures that once logged in, the user won’t have to log in again and again to access the needed service.
It’s the next security step that follows the authentication procedure. Your app’s microservices are going to need a confirmed verification that a client or another service is authorized to perform a particular action. Authorization solves the security problem of assigning access rights to resources of the distributed system to an appropriate user. Your microservices won’t have to deal with authentication and authorization forms and users’ credentials storage. For top security, you’ll have an identity and access management system.
You’ve probably heard of such famous authentication protocols as OpenID, OAuth/OAuth2, Kerberos, and good old SAML. Also, there are well-known identity and access management systems like Okta, Keycloak, and Shiro. All of these security tools are at your disposal.
Security Thing 2. API Gateway
API gateway allows your microservices to share the functionality with other apps over a defined UI existing between these applications and your own. The inputs and outputs of such UIs can be secured, unexposed, and internal to the apps’ modules. At the same time, they might be exposed outside the app’s ecosystem to receive and transmit data to other external UIs.
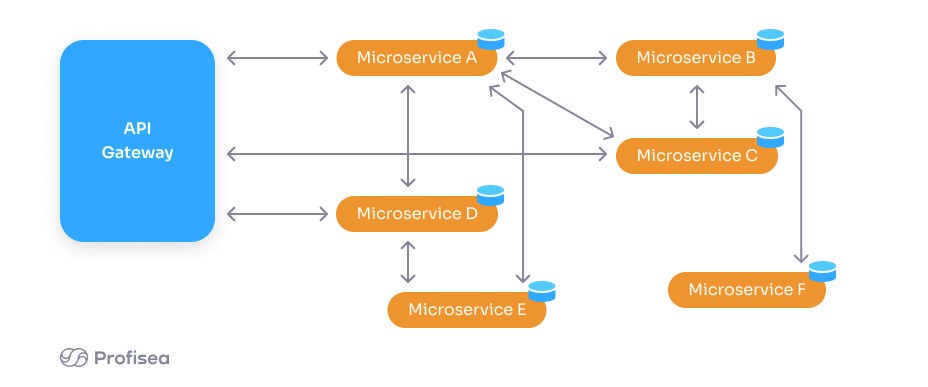
You’ll have to apply more scalable methods to secure your API than the centralized session management. Your gateway is usually responsible for dealing with both authentication and authorization procedures at the level of microservices. So, you should build your security model in a way to allow the delegation of tasks to the microservices level.
Security Thing 3. The Concept of Access Tokens
The previous paragraph leads us to another extra element of security that API gateways bring to microservices – token-based authentication. As the API shields the microservices from a client, a client can’t access any service directly or exploit it. This leads to the question of how a service communicates a client’s identity once it authenticates to the other microservices in a distributed system.
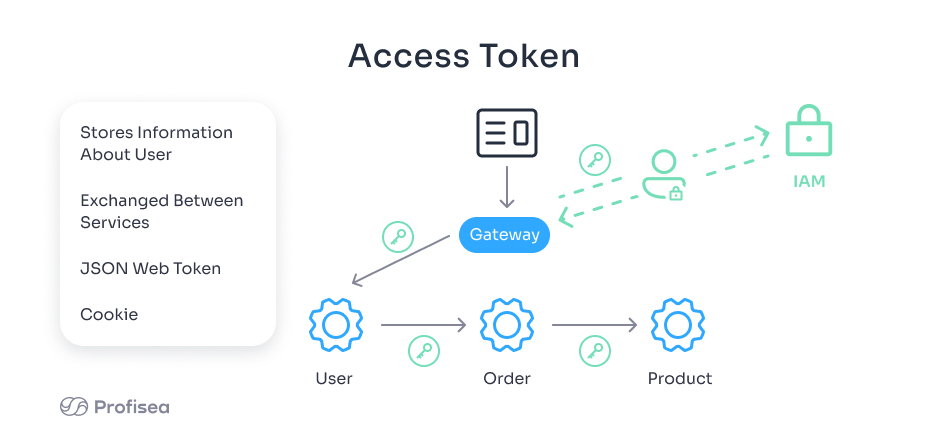
The solution is to use access tokens that allow you to record the clients’ credentials. The access tokens (e.g., JSON Web Token or session cookies) securely store users’ data and easily identify them each time they try to access the microservices system. API gateway forwards the client’s request to the server that assesses whether or not the client has permission to use the requested service.
 ||||
||||
An access token then exchanges the information about the client between other assigned services to let them determine if a token itself is valid. The microservices pull the client’s data out of the token and perform the verification procedure to ensure that the client is authorized to use the service. Each service can use the access token when calling other services.
The most important security thing is that the data stored in tokens has to be encrypted to prevent security breaches caused by any third-party applications. For example, JSON format is an open security standard that priori encrypts the access tokens and provides supporting libraries for various programming languages.
Securing Your Microservices Ecosystem
Consider the following best security practices when protecting your microservices ecosystem:
- Implement token-based authentication and access control mechanisms.
- Leverage IAM solutions to centralize identity and access management.
- Encrypt data in access tokens securely to prevent unauthorized access to microservices.
- Embrace DevOps practices to integrate security testing into your development lifecycle, thus enhancing your microservices security.
Securing your microservices ecosystem is a continuous process that requires vigilance and adaptation to evolving threats, maintaining the security of your microservices environment. If you face security challenges, seek expert guidance and consider partnering with security professionals who specialize in microservices security.
Remember, the security of your microservices architecture is not just a technical concern – it’s a fundamental aspect of delivering a reliable and trustworthy software product to your users, ensuring the security of your microservices applications.
Final Words: DevOps and Security in Microservices
Security patterns in microservices-based applications are to be kept in mind since you can’t leave your software product unprotected in any case, much less when your architecture is distributed. While API and authentication and authorization security technologies are a must-have, the token-based approach also has some tangible benefits to consider.
First of all, it stores and passes the identity of the caller between the microservices securely. What’s more, the security services can verify by themselves if the client is authorized to use their functionality.
In recent years, the DevOps approach has greatly improved security testing practices and integrated them into microservices and the development lifecycle. If you struggle with the matter of securing your microservices ecosystem, give us a call or send an email, and we’ll try to find the optimal security solution for your problem.




