eBPF: how DevOps brings ultimate observability and security to the Linux kernel
The extended Berkley Packet Filter (eBPF) is a powerful DevOps technology for executing custom bytecode securely within the Linux kernel without changing the kernel modules.
It has recently blown up as one of the greatest IT trends. In 2021, Microsoft, Google, Facebook, Netflix, and Isovalent launched the eBPF Foundation, which hosts all eBPF open-source projects. The community even plans to expand this revolutionary technology beyond Linux.
So, why do the IT giants cooperate to drive the growth of eBPF? How does this trendy DevOps technology improve networking, tracing, and observability? Why is the eBPF program considered to be the most secure solution? Let’s sort it all out.
eBPF: Rethinking the Linux kernel
Kernel space and user space are two distinct Linux memory areas. Because of its privileged status, Kernel space is always secured and allows running only reliable code. Conversely, user space is not as protected as the kernel. It runs regular applications and accesses hardware via system calls.
Engineers have always praised kernel space for implementing networking, observability, and security features, but it also presents significant difficulties. For example, when dealing with additional modules or modifying kernel source code, developers needed to cope with abstracted layers and debug intricate infrastructure. The eBPF tools were invented to solve these issues.
In fact, eBPF is a new version of the plain-old BPF technology created in the early 1990s for analyzing and filtering network traffic. The reason why mastering kernel-level capabilities over network traffic didn’t become such essential decades ago is pretty simple. Those workloads ran on bare metal or virtual machines, and traffic could be easily managed through firewalls.
Trends dramatically changed in 2013, when Docker made containers shine. Combined with Kubernetes, Docker empowered engineers’ software with valuable DevOps tools to filter and delicately control traffic. Thus, an extended version of BPF was released. EBPF provided new features to observe almost all kernel events, could store more data, and exchange information with the user space applications.
eBPF architecture: How magic happens
The eBPF technology executes the logic of the user space programs produced by the eBPF compiler (BCC) within the Linux kernel. The eBPF programs run when certain kernel events (hooks) happen:
- System Calls (inserted when you make requests from user space into the Linux kernel)
- Entry and Exit Function (to set up the kernel to run the module’s functions when they’re needed)
- Network Events (performed when packets are accepted)
- Kprobes (to collect Linux kernel debugging and performance data)
- Uprobes (to insert a breakpoint into an executable file)
- Helper Functions (to control processes when defined markers are attained).
Namely, the variety of kernel events locations is one of the greatest features of the eBPF architecture.
To provide kernel security, the eBPF program also passes verification, including executing the eBPF program in the virtual machine.
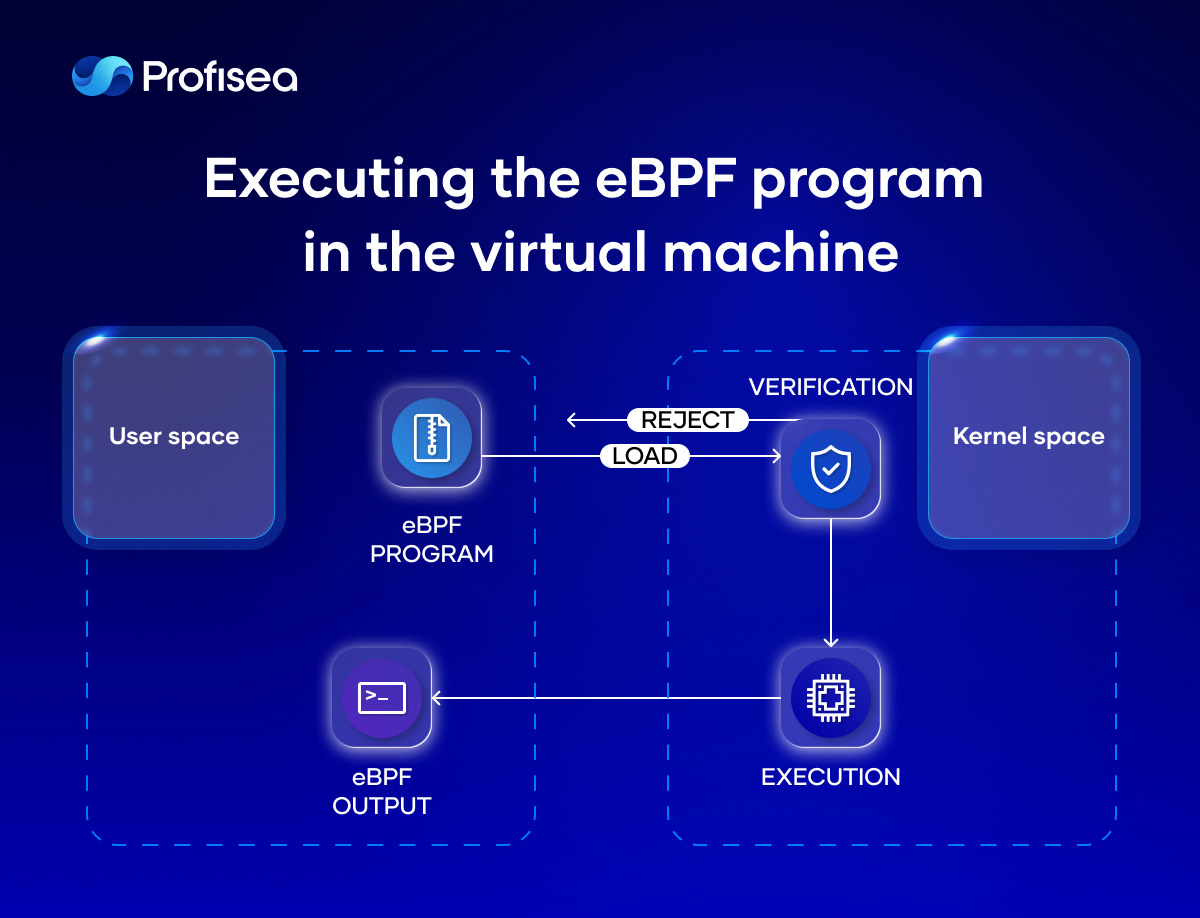
Another significant eBPF enhancement is the eBPF map that stores the application state and shares collected information. The eBPF technology provides various types of maps designed for very specific use cases:

The eBPF map is a key-value storage, where values are treated as binary blocks of arbitrary size and position in memory. These very specific eBPF map characteristics also make the eBPF technology feature-rich.
eBPF benefits
The benefits a company receives using the well-tuned eBPF technology are as follows:

The eBPF technology eliminates the necessity of transforming the kernel source code and enhances a software’s capacity to operate on different layers, bringing real magic into development, testing, deployment, and maintenance.
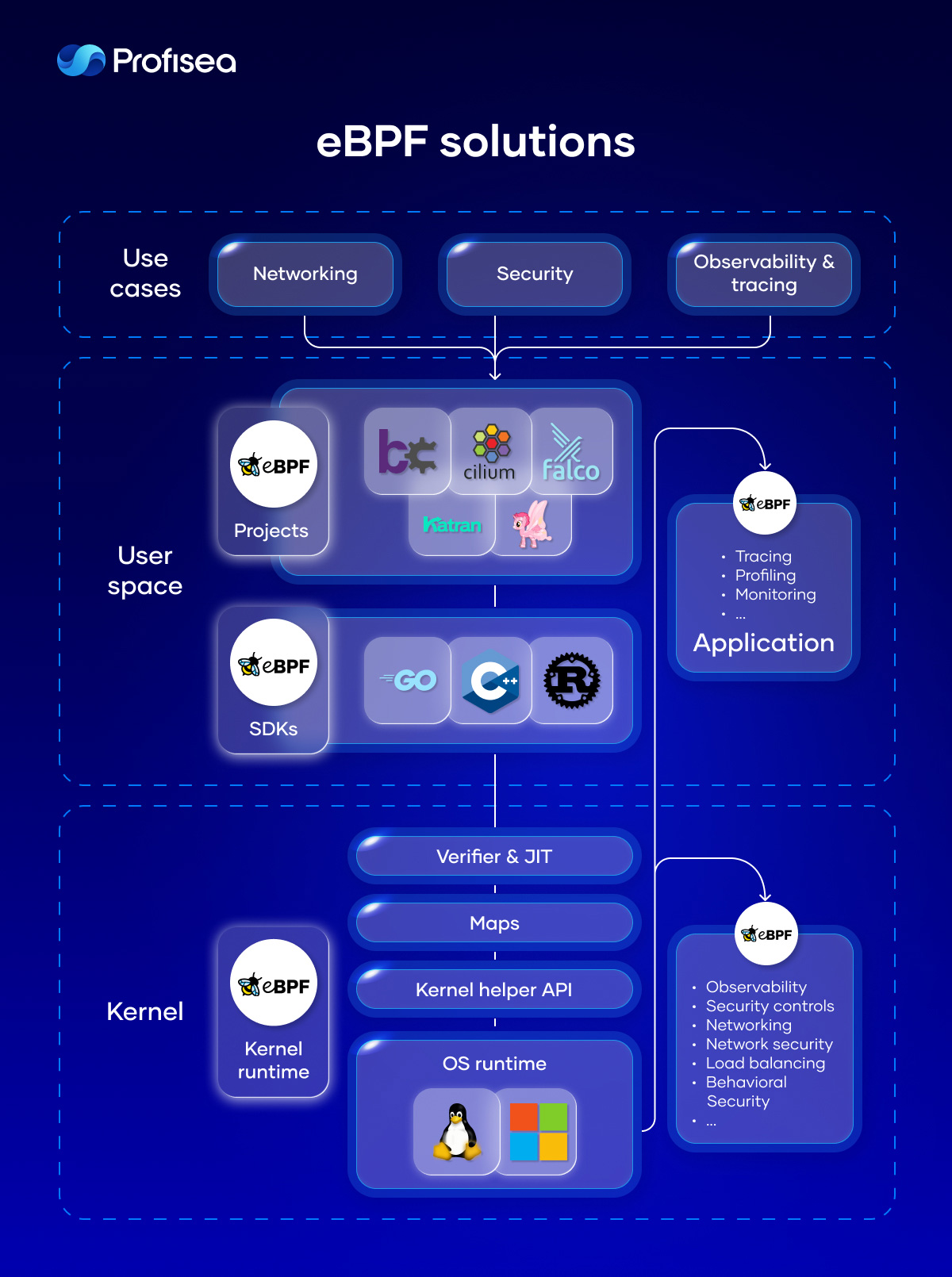
eBPF solutions
Today, many open-source tools use eBPF technology to increase system performance, observability, security, and networking.
Katran is an eBPF program to build a high-performance layer for load balancing with a re-engineered forwarding plane. It pulls XDP infrastructure from the kernel to provide an in-kernel facility for rapid packet processing.
DTrace and Hubble provide a comprehensive dynamic tracing framework for troubleshooting kernel and application problems on production systems in real time.
bcc is used for many tasks, including performance analysis and traffic control. It is mostly valued for the ability to attach eBPF programs to kprobes that provides instrumentation on a live kernel image. bpftrace compiles scripts to BPF-bytecode for interacting with the Linux BPF system, kernel dynamic tracing (kprobes), and user-level dynamic tracing (uprobes).
Falco is a very popular solution that uses different instrumentations to analyze the system workload and pass security events to userspace across containers, Kubernetes, and Cloud services.
Pixie is an open-source tool for Kubernetes to view the high-level state of your service maps, cluster resources, traffic, etc.
Pyroscope and Pa rka enable efficient CPU profiling of the whole Linux system, allowing eBPF programs to run inside of the kernel.
Tetragon provides powerful real-time, eBPF-based security runtime execution for Kubernetes.
Bumblebee is a solution that simplifies building, running, and distributing eBPF programs using OCI images.
Kepler (Kubernetes Efficient Power Level Exporter) uses eBPF to collect the power level consumption of the Kubernetes cluster and expose the data into Prometheus metrics.
Next steps
The eBPF solutions cooperate with kernel and user space, fundamentally changing the architecture of operating systems and infrastructure services approach. With eBPF solutions, your business will make a giant step forward in networking, security, profiling, tracing, and system observability.
Profisea implements only best DevOps practices, including game-changing eBPF technology, to bring advanced performance, security, tracing, and network observability into your software development lifecycle. Founded in Israel in 2015, Profisea has delivered numerous projects in various domains, constantly growing with our customers.
Feel free to contact Profisea’s top engineers to receive eBPF solutions that make OS kernel simple, programmable, scalable, and feature-rich with no overhead for your business.




